
Unveiling Magnetometer Privacy Risks: How Your Browser's Compass Can Expose You
The magnetometer, a sensor that measures magnetic field strength, is increasingly accessible to web browsers. While seemingly innocuous, it presents several privacy risks. This article explores potential vulnerabilities associated with browser access to magnetometer data and suggests mitigation strategies.
What is a Magnetometer and How Does it Work in Your Browser?
A magnetometer equips web browsers with the ability to read magnetic field strength via device sensors using the W3C Magnetometer API. Its intended uses range from controlling peripherals to creating compass apps or aiding indoor navigation.
The implementation is straightforward:
This code accesses magnetic field data around the device's axes (x, y, z) and computes the magnetic field magnitude. While implemented in browsers like Chrome (behind a flag), its security and privacy implications warrant careful consideration.
Magnetometer Privacy: Potential Risks Explored
Magnetometers are highly sensitive and could expose your data. Here's an outline of several key risks:
- Device Pairing and Covert Communication: Magnetometers can pair devices in proximity, and create covert communication channels using magnetic fields.
- Offline User Tracking and Location Tracking: Magnetometer data can track smartphones using beacon-like schemes, aiding location tracking (accuracy within 10 meters) and contact tracing efforts. Fusing magnetometer data with other sensors, like light sensors, can further refine indoor positioning by using unique magnetic fingerprints within buildings.
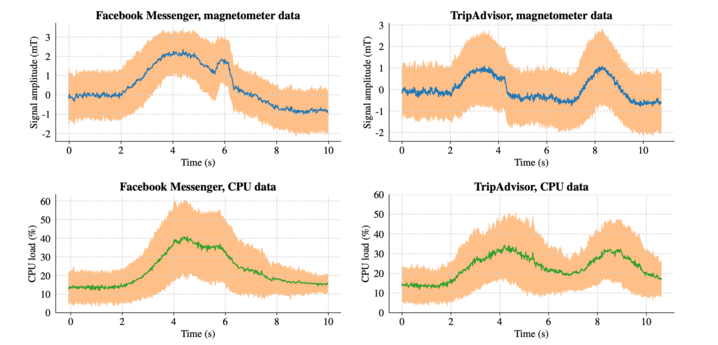
- Web Browsing History Leaks: Magnetic field readings may reveal user activity: which apps are in use, or which website the user is visiting. Changes in CPU workload create disturbances in the magnetic field by creating fingerprints of apps or accessed websites.
Real-World Scenarios: Magnetometer Abuse
Magnetometer abuses might require specialized infrastructure, here are a few examples. Imagine:
- Retail Tracking: Beacons in stores track customer movement.
- Highway Monitoring: Gates on motorways monitor driver behavior.
Studies show that smartphones on the driver's side register higher EMF readings due to proximity to electronically charged vehicle components, potentially identifying the driver.
Key Privacy Risks Summarized
- Location Tracking: Detecting user movement, particularly when combined with other sensors.
- Profiling Risks: Analyzing patterns of magnetic field changes.
- Correlation with Hardware: Linking magnetometer readings to CPU activity, potentially revealing app usage or websites visited.
Safeguarding Your Privacy: Mitigation Strategies
To address these risks, consider these mitigation strategies:
- Web Browser Permissions: Implement browser permissions to control magnetometer access.
- Frequency Capping: Limit the frequency of sensor readouts (e.g., to 1 Hz).
- Precision Reduction: Decrease readout value precision where feasible.
- User Permissions: Following explicit user permission (following a user prompt), some of the risks are mitigated. However, a website with access to the magnetometer sensor could still use the sensor.
Final Thoughts: Balancing Functionality and Privacy
Analyzing the privacy implications of sensors like magnetometers is crucial. Balancing functionality with privacy requires ongoing analysis, thoughtful design, and robust standards.


