Stop Websites From Spying: Protecting Your Data with Generic Sensor API Controls
Are you concerned about websites tracking your every move? The Generic Sensor API in your smartphone, smartwatch, or laptop can expose sensitive data about your location, environment, and even your physical movements. This article dives deep into how these sensors work and how JShelter can help you regain control of your privacy.
Understanding the Generic Sensor API: What Data is at Risk?
Modern devices are packed with sensors that gather information about the world around them. While this technology enables useful features, it also creates potential privacy risks. The Generic Sensor API provides websites with a unified way to access these sensors, potentially revealing a surprising amount of personal information.
What You Need to Know:
- Diverse Sensors: From geolocation to orientation, devices use various sensors to collect data.
- Accessibility: The Generic Sensor API allows websites to tap into this data stream.
- Privacy Concerns: Unfettered access raises serious risks of tracking and fingerprinting.
Browser Support for Sensor APIs
The level of sensor API support greatly varies depending on your browser, OS, and device. For instance, while some APIs might be fully functional in Chrome on Android, they might be experimental or entirely absent in other browsers. This inconsistency presents a fragmentation challenge for web developers aiming to leverage sensor data across different platforms.
Key Considerations
- Platform Dependencies: Each platform handles API implementation differently.
- Feature Flags: Experimental features often require manual enablement through browser settings.
Sensor Types: Low-Level vs. High-Level
Sensors fall into two main categories: low-level and high-level. Understanding the difference is crucial for assessing privacy risks.
Low-Level Sensors: Direct Hardware Access
- Examples: Gyroscope, Magnetometer, Accelerometer
- Function: These sensors directly measure physical properties.
High-Level Sensors: Abstracted Data
- Examples: GeolocationSensor, AbsoluteOrientationSensor
- Function: These sensors combine data from multiple sources (sensor fusion) to provide higher-level information.
The Threat of Device Fingerprinting: How Sensors Expose Your Identity
The W3C recognizes the risk of using the Generic Sensor API for device fingerprinting. Subtle variations in sensor behavior, caused by manufacturing imperfections, can create unique identifiers for your device.
Why This Matters:
- Unique Identifiers: Small differences in sensor readings can be used to identify your specific device.
- Privacy Violation: Fingerprinting allows websites to track you across the web without your consent.
Concrete Examples of Sensor Vulnerabilities
Dive into the specific vulnerabilities of each sensor and how they can be exploited to gather information about you.
Leaking Boot Time with Timestamps
The Sensor.timestamp attribute reveals the device's last boot time with millisecond precision. This seemingly innocuous piece of information can be used to create a unique fingerprint, especially for devices that have been running for an extended period.
JShelter Solution:
- Timestamp Normalization: JShelter modifies the time origin to the page context creation time.
- Unique Readings: Ensures timestamps still uniquely identify each reading within the same page.
Global Orientation Settings, Yaw, Pitch and Roll
Many sensor classes depend on device orientation for accurate readings. JShelter ensures that even faked readings appear realistic by using a shared orientation model.
Understanding Orientation:
- Axis Orientation: The article defines the x, y, and z axes for a typical mobile phone.
- Yaw, Pitch, Roll: These three values define the rotation of the device in 3D space.
- Earth Reference: The phone's rotation is related to the Earth's coordinate system.
How JShelter Fakes Orientation:
- Pseudorandom Values: Yaw, pitch, and roll are randomly generated using a seeded PRNG.
- Deterministic Behavior: The domain hash ensures consistent values for a given website.
- Rotation Matrix: A rotation matrix is calculated and shared between sensor wrappers.
AmbientLightSensor: Exposing your environment
The AmbientLightSensor measures the amount of light in your surroundings. While intended to adjust screen brightness, this data can be exploited to infer user behavior and even steal PINs.
Risks:
- Behavioral Analysis: Reveals work habits, lighting preferences, and movement patterns.
- Distance Calculation: Using the inverse square law, attackers can estimate the distance to light sources.
PIN Skimming: A Serious Threat
Attackers can analyze shadows cast by fingers to detect PINs entered on the device. Studies have shown high accuracy rates in PIN detection using ambient light sensor data.
More Threats:
- TV Channel Identification: Detects TV channels and on-demand videos being watched.
- Cross-Device Tracking: Correlates light sensor data from multiple devices in the same room.
- Cross-Device Communication: Uses light emitted from one device to transmit messages to another.
JShelter's Approach:
- Fake Readings: Generate fake illuminance values instead of modifying real ones.
- Realistic Simulation: Mimics the behavior of a stationary device under constant light conditions.
- Pseudorandom Value: Uses a PRNG seeded with the domain hash to generate a consistent illuminance value.
Accelerometer: Tracking Your Movements
Accelerometers measure the rate of change of velocity. This data can reveal how the device is being used, including whether the user is lying down, walking, or cycling.
Threats:
- Trajectory Inference: Determines the device's position by analyzing movement patterns.
- Activity Recognition: Identifies whether the user is lying, sitting, walking, or cycling.
- Walking Pattern Analysis: Determines human walking patterns, and identifies users by the way they walk.
- Speech Recognition: Vulnerable to Spearphone attacks, enabling gender classification and speaker identification.
JShelter's Defense:
- Stationary Device Simulation: Wrappers simulate a stationary device, potentially rotated.
- Rotation Matrix: Uses a shared rotation matrix to maintain consistent behavior across sensors.
- Gravity Vector Faking: Generates a fake gravity vector based on the device's orientation.
Linear Acelleration Sensor: Faking Vibrations
- The LinearAccelerationSensor returns acceleration values without the contribution of gravity and returns close to zero
- JShelter simulates small vibrations to make it look more believable without revealing real data
Accelerometer: Combining the Sensors
- By combining the LinearAccelerationSensor and the GravitySensor it simulates the device's movements.
Gyroscope: Capturing Angular Velocity
Gyroscopes measure the angular velocity of the device along the x, y, and z axes. This data can be used for speech recognition and fingerprinting.
How It's Exploited:
- Stationary Device Fingerprinting: Resonance from internal and external sounds affects angular velocities, creating a unique fingerprint.
- Walking Pattern Analysis: Gyroscope data can be used to analyze human walking patterns for moving devices.
JShelter's Solution:
- Zero Velocity Simulation: Simulates a stationary device with velocities oscillating slightly around zero.
- Pseudorandom Intervals: Applies changes in pseudorandom intervals to mimic real-world sensor imperfections.
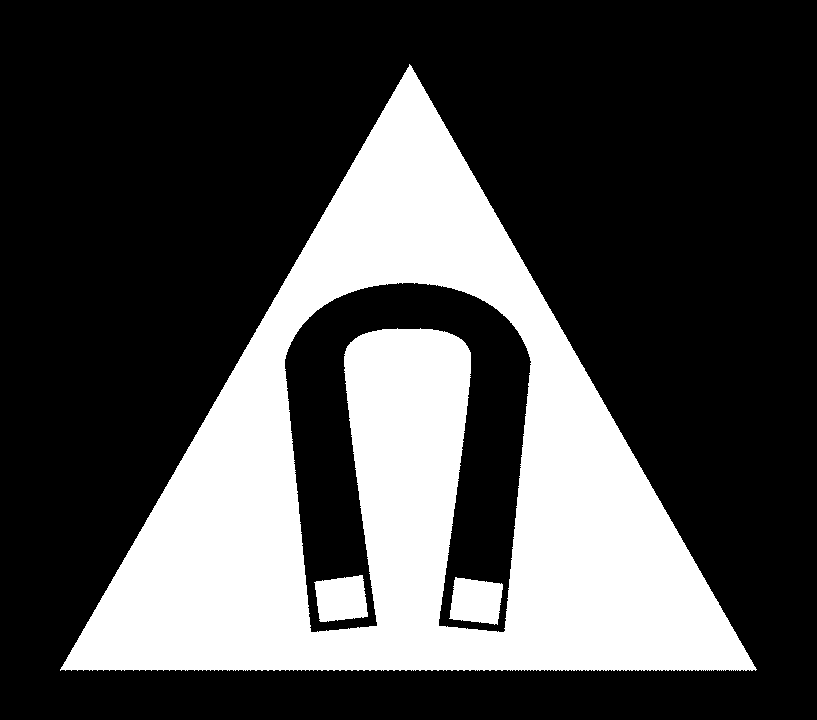
Magnetometer: Exposing Your Location
Magnetometers measure the strength and direction of the magnetic field around the device. While the Earth's magnetic field varies by location, interference from other devices and buildings makes it difficult to pinpoint a user's exact location.
Risks:
- Location Tracking: Although not precise, magnetometer data can provide clues about the device's location.
- Interference: Readings are easily influenced by nearby electronic devices and structures.
JShelter's Protection:
(The article extract ends before detailing JShelter's magnetometer protection, but the general method would be to fake location data, like it does for the other sensors.)
Stay Protected with JShelter
By understanding the risks associated with the Generic Sensor API and using tools like JShelter, you can take control of your privacy and prevent websites from tracking your every move. Stay informed, stay protected.
JShelter is supported by: